According to ITNews , Quarkslab warned that these security holes can be exploited by unauthenticated remote attackers on the same local network, and in some cases, even remotely. The researchers said the impacts of these vulnerabilities include DDoS, information leakage, remote code execution, DNS cache poisoning, and network session hijacking.
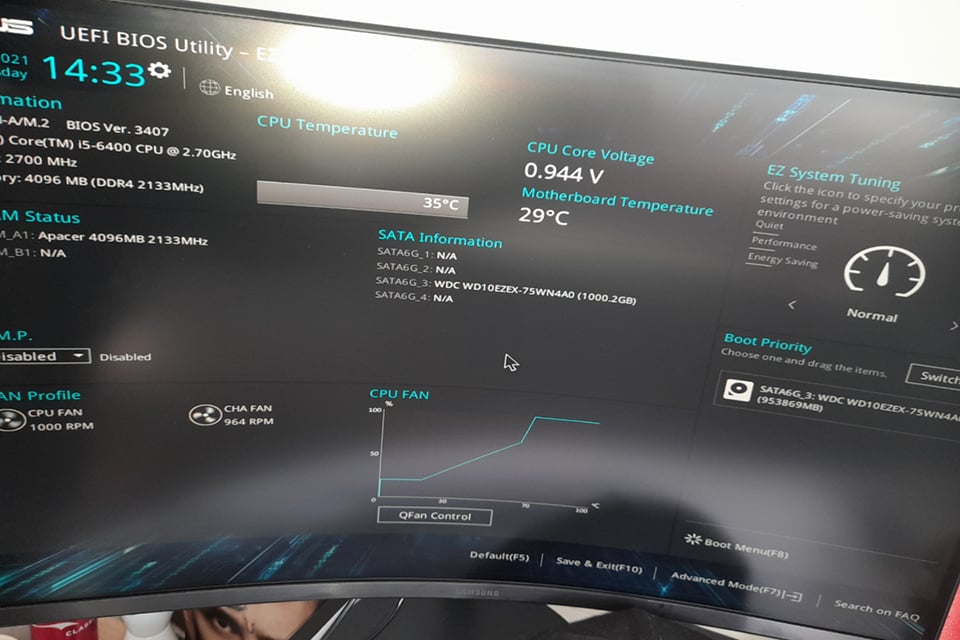
UEFI is the most commonly used BIOS system.
The CERT Cybersecurity Coordination Center at Carnegie Mellon University (USA) said that this error was identified in the implementation process from UEFI vendors, including American Megatrends, Insyde Software, Intel and Phoenix Technologies, while Toshiba was not affected.
Insyde Software, AMI, and Phoenix Technologies have all confirmed to Quarkslab that they are providing fixes. Meanwhile, the bug is still being investigated by 18 other vendors, including big names like Google, HP, Microsoft, ARM, ASUSTek, Cisco, Dell, Lenovo, and VAIO.
The flaws reside in the EDK II TCP/IP stack, NetworkPkg, which is used for network booting and is particularly important in data centers and HPC environments for automating early boot phases. The three most severe flaws, all with CVSS scores of 8.3, are related to DCHPv6 handler buffer overflows, including CVE-2023-45230, CVE-2023-45234, and CVE-2023-45235. The other flaws have CVSS scores ranging from 5.3 to 7.5.
Source link


![[Photo] Closing of the 11th Conference of the 13th Central Committee of the Communist Party of Vietnam](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/4/12/114b57fe6e9b4814a5ddfacf6dfe5b7f)
































![[Photo] Overcoming all difficulties, speeding up construction progress of Hoa Binh Hydropower Plant Expansion Project](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/4/12/bff04b551e98484c84d74c8faa3526e0)



























































Comment (0)