| The cyber attack on the VNDIRECT system on March 24 was identified as a data encryption malware attack - ransomware. This type of attack is a major concern for businesses and organizations in the digital age. To help readers learn more about ransomware attacks, the level of danger, and how to prevent and respond, VietNamNet has produced a series of articles "The existential danger from data encryption attacks". |
Extending the "nightmare" of data encryption malware
The cyber attack on the VNDIRECT system, a company in the top 3 of the Vietnamese stock market, which occurred on the morning of March 24 has now been basically resolved. The data has been decoded and the My Account lookup system is back in operation.
VNDIRECT reported that the incident on March 24 was carried out by a professional attack group, causing all company data to be encrypted. Data encryption malware attacks - ransomware have always been a nightmare for businesses and organizations around the world in recent years, due to the serious consequences it can cause. Experts also liken ransomware to a "nightmare" and "ghost" in cyberspace.
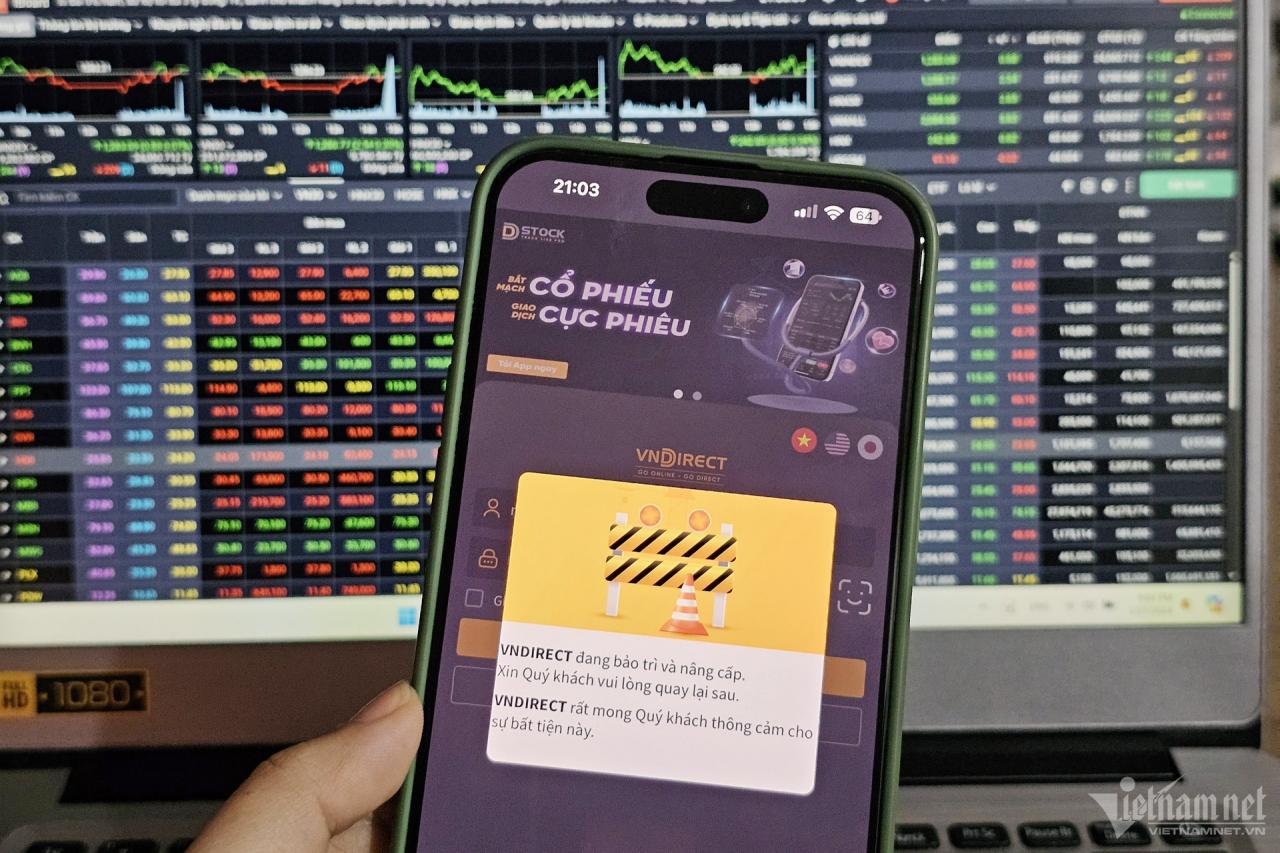
According to the roadmap VNDIRECT announced to customers and partners, the operating unit will continue to gradually reopen systems, products and other utilities. This unit plans to check the flow with the stock exchanges on March 28.
However, from the analysis of information security experts, it can be seen that the hard days of VNDIRECT technology team and experts scanning for vulnerabilities and thoroughly fixing the problem are still long. Ransomware is not a new form of cyber attack but it is very complicated, requiring a lot of time to clean up data, completely restore the system, and bring back normal operations.
“To completely fix a ransomware attack, sometimes the operating unit has to change the system architecture, especially the backup system. Therefore, with the incident that VNDIRECT is facing, we think it will take more time, even months, for the system to fully recover,” said NCS Technical Director Vu Ngoc Son.
Mr. Nguyen Minh Hai, Technical Director of Fortinet Vietnam, said that depending on the severity of the attack, the ability to prepare in advance and the effectiveness of the response plan, the time required to recover the system after a ransomware attack can vary greatly, from a few hours to several weeks for complete recovery, especially in cases where a large amount of data needs to be recovered.
“Part of this recovery process includes ensuring that the data encryption malware has been completely removed from the network and that no backdoors have been left behind that could allow attackers to regain access,” said Nguyen Minh Hai.
Experts also commented that, in addition to being a "wake-up call" for the units managing and operating important information systems in Vietnam, the cyber attack on VNDIRECT also once again showed the danger level of ransomware.
More than 6 years ago, WannaCry and its variants of data encryption malware caused many businesses and organizations to "struggle" when they quickly spread to more than 300,000 computers in nearly 100 countries and territories around the world, including Vietnam.
In recent years, businesses have always been concerned about ransomware attacks. Last year, Vietnam's cyberspace recorded many ransomware attacks with serious consequences; in which, there were cases where hackers not only encrypted data to demand ransom, but also sold the data to third parties to maximize the amount of money collected. According to NCS statistics, in 2023, up to 83,000 computers and servers in Vietnam were recorded to be attacked by ransomware.
Common 'paths' to penetrate the system
VNDIRECT's technology team is working with information security experts to deploy solutions to fully restore the system while ensuring system safety. The cause of the incident and the 'path' that the hacker used to penetrate the system are still under investigation.
According to Mr. Ngo Tuan Anh, CEO of SCS Smart Network Security Company, to attack data encryption, hackers often choose to penetrate the server containing important data and encrypt the data. There are 2 ways that hackers often use to penetrate the system of units, which are directly through the vulnerabilities and weaknesses of the server system; or choose to "go around" through the administrator's computer and from there take control of the system.

Talking to VietNamNet , Mr. Vu The Hai, Head of Information Security Monitoring Department, VSEC Company also pointed out some possibilities for hackers to infiltrate and install malware into the system: Exploiting existing vulnerabilities on the system to take control, install malware; sending emails with attached files containing malware to trick users in the open system, activating malware; logging into the system from leaked passwords or weak passwords of system users.
Expert Vu Ngoc Son analyzed that with ransomware attacks, hackers often enter the system through a number of ways such as password probing, exploiting system vulnerabilities, mainly zero-day vulnerabilities (vulnerabilities that the manufacturer has not yet patched - PV).
"Financial companies usually have to meet regulatory standards, so the possibility of password discovery is almost impossible. The most likely possibility is an attack through a zero-day vulnerability. Accordingly, hackers remotely send error-causing data segments that cause the software to fall into an uncontrolled state when processed.
Next, the hacker runs remote code execution and takes control of the service server. From this server, the hacker continues to collect information, uses the obtained administrative accounts to attack other servers in the network, and finally runs data encryption tools for extortion," expert Vu Ngoc Son analyzed.
| A new survey conducted by security firm Fortinet among businesses in the Asia-Pacific region, including Vietnam, shows that: Ransomware is still a major concern. Extortion through ransomware attacks is the top cybersecurity concern for manufacturers, with 36% of surveyed organizations reporting experiencing a ransomware attack in the past year, up 23% from Fortinet's similar survey in 2020. |
Lesson 2 - Experts show how to respond to ransomware attacks
Source

























































































Comment (0)