Security experts have discovered a malicious campaign that steals OTP codes on Android devices globally, by infecting thousands of Telegram bots with malware.
Researchers at security firm Zimperium discovered the malicious campaign and have been tracking it since February 2022. They report that they have detected at least 107,000 different malware samples associated with the campaign.
The malware tracks messages containing OTP codes from more than 600 global brands, some with hundreds of millions of users. The hackers' motive is financial.
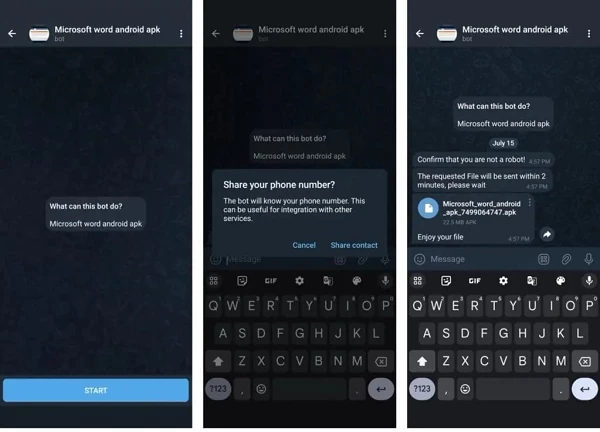 |
| Telegram Bot Asks Users to Provide Phone Number to Send APK File |
According to Zimperium, SMS stealer malware is distributed via malicious ads or Telegram bots that automatically communicate with victims. There are two scenarios that hackers use to attack.
Specifically, in the first case, the victim will be tricked into accessing fake Google Play sites. In the other case, the Telegram bot promises to give users pirated Android apps, but first, they must provide a phone number to receive the APK file. This bot will use that phone number to create a new APK file, allowing the hacker to track or attack the victim in the future.
Zimperium said the malicious campaign used 2,600 Telegram bots to promote various Android APKs, which were controlled by 13 Command & Control servers. Victims were spread across 113 countries, but most were from India and Russia. The US, Brazil, and Mexico also had significant numbers of victims. These numbers paint a worrying picture of the large-scale and highly sophisticated operation behind the campaign.
Experts discovered that the malware transmits captured SMS messages to an API endpoint at the website 'fastsms.su'. This website sells access to virtual phone numbers abroad, which can be used to anonymize and authenticate online platforms and services. It is likely that infected devices were exploited without the victim's knowledge.
Additionally, by granting access to SMS, victims give malware the ability to read SMS messages and steal sensitive information, including OTP codes during account registration and two-factor authentication. As a result, victims may see their phone bills skyrocket or be unwittingly involved in illegal activities, tracing their devices and phone numbers.
To avoid falling into the trap of bad guys, Android users should not download APK files outside of Google Play, not grant access to unrelated applications, and ensure Play Protect is enabled on the device.
Source: https://baoquocte.vn/canh-bao-chieu-tro-danh-cap-ma-otp-tren-thiet-bi-android-280849.html






![[Photo] Ministry of Defense sees off relief forces to the airport to Myanmar for mission](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/3/30/245629fab9d644fd909ecd67f1749123)
![[Photo] Prime Minister Pham Minh Chinh chairs meeting to remove difficulties for projects](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/3/30/7d354a396d4e4699adc2ccc0d44fbd4f)






















































































![[REVIEW OCOP] An Lanh Huong Vet Yen Cat](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/3/27/c25032328e9a47be9991d5be7c0cad8c)



Comment (0)