The software giant said two of these vulnerabilities were classified by Microsoft as critical (involving Windows Kerberos security bypass and remote code execution in Hyper-V). The patch includes fixes for 10 elevation of privilege vulnerabilities, 12 remote code execution vulnerabilities, 11 information disclosure vulnerabilities, 6 denial of service (DoS) vulnerabilities, and more.
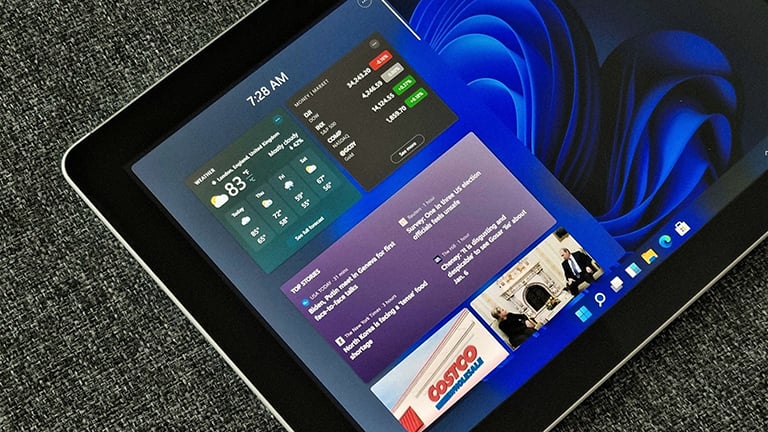
New update helps patch many security vulnerabilities in Microsoft products
While the January security patch does not contain fixes for vulnerabilities that are actively being exploited by attackers, some are particularly known, including CVE-2024-20674, which allows the Windows Kerberos security feature to be bypassed (critical), CVE-2024-20700 in the Hyper-V hardware virtualization system that can be exploited to execute remote code on the system (critical), and CVE-2024-20677 in Microsoft Office that allows remote code execution using specially configured malicious Office documents that contain 3D FBX models. To address this issue, Microsoft has disabled the ability to insert FBX files into Word, Excel, PowerPoint, and Outlook for Windows and macOS.
Users can find the fixed vulnerabilities on Microsoft's official website. In addition, the software giant has started distributing cumulative updates for Windows 11 (KB5034123) and Windows 10 (KB5034122).
For Windows devices with multiple monitors, users may experience issues when using the Copilot AI virtual assistant (in preview) with shortcuts suddenly switching between screens or being misaligned. The developers plan to release a patch to address this. Additionally, there is currently no support for Copilot in preview versions of Windows when the taskbar is positioned vertically. To access Copilot, users must ensure the taskbar is positioned horizontally at the bottom or top of the workspace.
Source link


![[Photo] Promoting friendship, solidarity and cooperation between the armies and people of the two countries](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/4/17/0c4d087864f14092aed77252590b6bae)
![[Photo] Closing of the 4th Summit of the Partnership for Green Growth and the Global Goals](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/4/17/c0a0df9852c84e58be0a8b939189c85a)
![[Photo] Nhan Dan Newspaper announces the project "Love Vietnam so much"](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/4/17/362f882012d3432783fc92fab1b3e980)
![[Photo] General Secretary To Lam receives French Ambassador to Vietnam Olivier Brochet](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/4/17/49224f0f12e84b66a73b17eb251f7278)
![[Photo] National Assembly Chairman Tran Thanh Man meets with outstanding workers in the oil and gas industry](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/4/17/1d0de4026b75434ab34279624db7ee4a)





















![[Photo] Welcoming ceremony for Chinese Defense Minister and delegation for friendship exchange](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/4/17/fadd533046594e5cacbb28de4c4d5655)




























![[Video] Viettel officially puts into operation the largest submarine optical cable line in Vietnam](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/4/17/f19008c6010c4a538cc422cb791ca0a1)







































Comment (0)