Numerous ransomware attack groups are targeting systems in Vietnam.
Data recorded from the technical systems of the National Cybersecurity Monitoring Center (NCSC) under the Information Security Department (Ministry of Information and Communications) as well as the National Cybersecurity Center under A05 ( Ministry of Public Security ) all indicate that recently, ransomware attack groups have been focusing their attacks on Vietnamese organizations and businesses.
Since the end of March, while ransomware attacks on information systems in Vietnam have been on the rise, the Cybersecurity Department announced on April 6th that ransomware attacks targeting agencies, organizations, and businesses in Vietnam are now appearing in cyberspace.
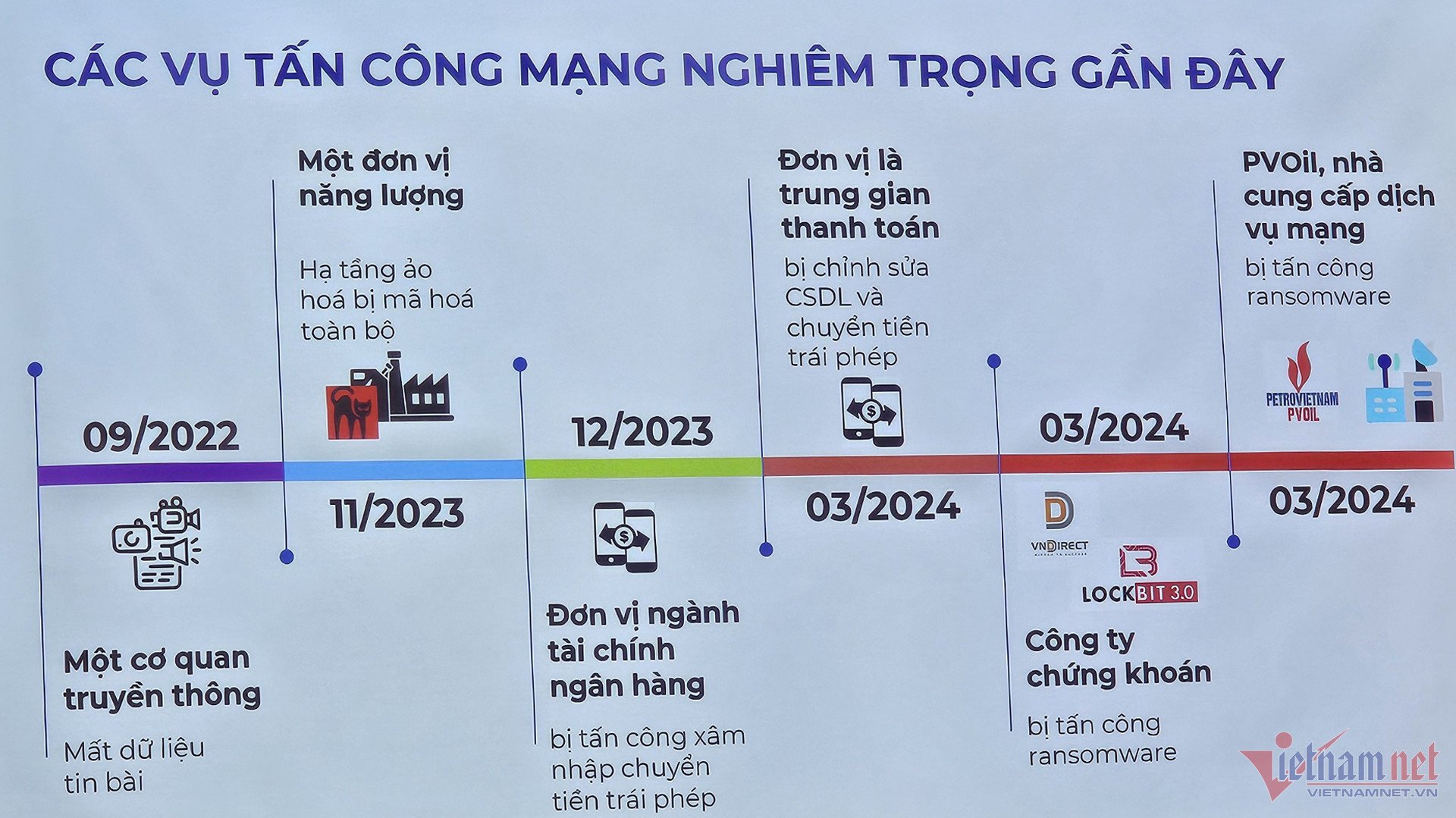
The NCSC's monitoring system also noted that ransomware attack groups are focusing more on organizations operating in the financial, banking, energy, and telecommunications sectors. In fact, ransomware attacks on the systems of several Vietnamese businesses in recent days have caused damage to assets, affected brand reputation, and especially disrupted the business operations of these entities.

Speaking on the sidelines of the seminar "Preventing ransomware attacks" held on April 5th, Mr. Pham Thai Son, Deputy Director of NCSC, stated that through analysis and identification of the causes and targets of recent attacks on information systems in Vietnam, the Cybersecurity Department has found that many different attack groups are targeting the systems of domestic organizations and businesses, such as Lockbit, Blackcat, Mallox, etc.
Representatives from the NCSC also stated that while ransomware attacks have existed for a long time, the level of sophistication, complexity, and professionalism of these attack groups is now much higher than before. Meanwhile, although Vietnam is accelerating its digital transformation and many activities are shifting to the digital environment, many domestic organizations and businesses still do not adequately secure their information systems, making them easy targets for hacker groups.
Mr. Pham Thai Son also shared that the Information Security Department regularly and continuously issues warnings about new vulnerabilities and new attack trends to agencies, organizations, and businesses so that they can update and address errors promptly. However, in reality, many organizations and businesses have not really paid attention to addressing these issues, nor have they invested adequately to ensure information security.
According to statistics, after more than 7 years since the Law on Cybersecurity and Decree 85 on ensuring information system security according to security levels came into effect, more than 33% of information systems of state agencies have not yet completed the approval of information system security levels, and the percentage of systems that have fully implemented protection measures according to the proposed security level is even lower, only about 20%.
Sharing the same view, representatives from the National Cybersecurity Center, Department A05, also stated: The cybersecurity situation in Vietnam is becoming increasingly complex, with a higher frequency of attacks and greater losses. About 2-3 years ago, hackers stealing 40-50 billion VND was considered a significant amount, but now there are cyberattacks causing losses of up to 200 billion VND.
Emphasizing that Vietnam is actively undergoing digital transformation but many organizations have not paid sufficient attention to cybersecurity, a representative from the National Cybersecurity Center also pointed out several serious attacks on entities in the media, energy, finance, banking, payment intermediaries, and securities sectors that occurred in Vietnam's cyberspace from September 2022 to April 2024, with an increase in scale and frequency of attacks.
Paying a ransom for data will set a bad precedent.
Notably, despite sharing the common assessment of the extreme danger of ransomware attacks—that once data is encrypted, there is virtually no chance of decryption, with a recovery rate close to zero—experts still recommend that agencies and organizations not pay hackers to ransom encrypted data.
Representatives from the National Cybersecurity Center stated that all parties involved in the global anti-ransomware initiative agree on the need to encourage entities not to pay, as this would create demand and encourage cyberattack groups to focus their attacks more intensely.
“If organizations remain resilient in the face of attacks, the motivation of hacker groups will decrease. Last March, a company in Vietnam paid a ransom to restore its system. We warned that this would set a bad precedent for that company and other businesses in the market. Currently, there are no specific regulations, so whether or not to pay a ransom for data remains a choice for businesses and organizations,” a representative from the National Cybersecurity Center shared.

Speaking to a VietNamNet reporter about this issue, expert Vu Ngoc Son, Technical Director of NCS Company, also stated: The general trend worldwide is to try not to pay ransom to hackers, to avoid setting a bad precedent because this action could encourage hackers to attack other targets domestically or encourage other hacker groups to continue attacking businesses and organizations that pay ransoms.
The general advice from authorities and experts is that businesses and organizations should "prevent rather than fight" when facing ransomware attacks. In the "Handbook on Preventing and Mitigating Risks from Ransomware Attacks," released on April 6th, the Cybersecurity Department recommended nine measures that businesses can proactively take to prevent this dangerous type of attack.

Source








































































































Comment (0)