According to The Hacker News , cyberattacks targeting Meta Business and Facebook accounts have become more common over the past year thanks to the Ducktail and NodeStealer malware, which are used to attack businesses and individuals active on Facebook. Among the methods used by cybercriminals, social engineering plays a major role.
Victims are approached through a variety of platforms, from Facebook, LinkedIn to WhatsApp and freelance job portals. Another known distribution mechanism is search engine poisoning to lure users into downloading fake versions of CapCut, Notepad++, ChatGPT, Google Bard and Meta Threads, among others, which are versions created by cybercriminals to implant malware on victims’ machines.
It is common for cybercriminal groups to use URL shortening services and Telegram for command and control, and legitimate cloud services like Trello, Discord, Dropbox, iCloud, OneDrive, and Mediafire to host malware.
The actors behind Ducktail lure victims with marketing and branding projects to compromise the accounts of individuals and businesses operating on Meta’s business platform. Potential targets are directed to fake posts on Upwork and Freelancer via Facebook or LinkedIn InMail ads that contain links to malicious files disguised as job descriptions.
Researchers at Zscaler ThreatLabz say Ducktail steals cookies from browsers to hijack Facebook business accounts. The spoils of this operation (hacked social media accounts) are sold to the underground economy, where they are priced according to their usefulness, typically ranging from $15 to $340.
Several infection chains observed between February and March 2023 involved the use of shortcuts and PowerShell files to download and launch malware, demonstrating continued evolution in the attackers' tactics.
These malicious activities were also updated to collect users' personal information from X (formerly Twitter), TikTok Business, and Google Ads, as well as leverage stolen Facebook cookies to generate fraudulent ads in an automated manner and elevate privileges to perform other malicious activities.
The method used to take over the victim's account is to add the hacker's email address to the account, then change the victim's password and email address to lock them out of the service.
Security firm WithSecure said a new feature observed in Ducktail samples since July 2023 is the use of RestartManager (RM) to kill processes that lock the browser database. This feature is often found in ransomware, because files used by processes or services cannot be encrypted.
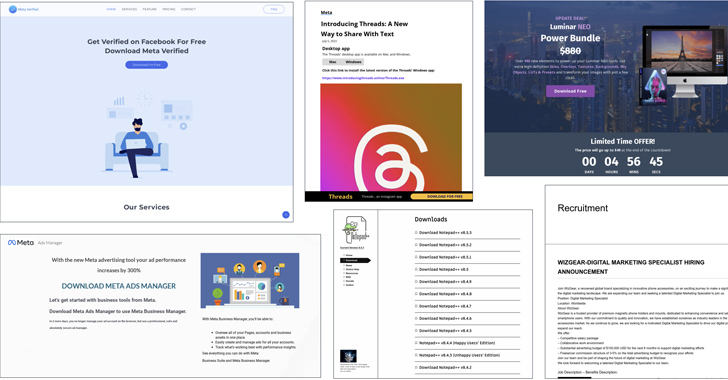
Some fake ads are designed to trick victims into downloading and executing malware on their computers.
Researchers at Zscaler said they found infections from compromised LinkedIn accounts belonging to users working in digital marketing, some with more than 500 connections and 1,000 followers, which helped facilitate the cybercriminals' scams.
Ducktail is believed to be one of many malware strains that Vietnamese cybercriminals are exploiting to carry out fraudulent schemes. There is a Ducktail clone called Duckport, which has been stealing information and hijacking Meta Business accounts since late March 2023.
The strategy of the cybercriminal group using Duckport is to lure victims to websites related to the brand they impersonate, then redirect them to download malicious files from file hosting services like Dropbox. Duckport also has new features, expanding its ability to steal information and hijack accounts, take screenshots, or abuse online note-taking services to replace Telegram to send commands to the victim's machine.
Researchers say that threats in Vietnam have a high degree of overlap in capabilities, infrastructure, and victims. This shows a positive relationship between criminal groups, shared tools, and tactics, techniques, etc. This is almost an ecosystem similar to the ransomware-as-a-service model but focused on social media platforms such as Facebook.
Source link


































![[Photo] Prime Minister Pham Minh Chinh works with the Standing Committee of Thai Binh Provincial Party Committee](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/5/12/f514ab990c544e05a446f77bba59c7d1)
![[Photo] Prime Minister Pham Minh Chinh receives Swedish Minister of International Development Cooperation and Foreign Trade](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/5/12/ae50d0bb57584fd1bbe1cd77d9ad6d97)

































































Comment (0)