A series of pager explosions in Lebanon, triggered by remote-controlled devices, has highlighted the security threat posed by the "weaponization" of everyday objects.
 |
| A radio device exploded in Baalbek, Lebanon, on September 18. (Source: Anadolu) |
The recent attacks in Lebanon, carried out using explosive-laden pagers and walkie-talkies, represent a new tactic and pose a significant security challenge to all countries worldwide .
The unique aspect of this tactic is not technological sabotage aimed at the enemy. Historically, the "Trojan horse" tactic has been used by exploiting communications or military equipment to then target specific objectives.
Software-based targeting
The attacks in Lebanon are highly controversial because the explosions used devices that are widely used in people's daily lives. These attacks in Lebanon killed 37 people, including two children, along with several Hezbollah commanders, and injured nearly 3,000 others.
International humanitarian law experts have accused the attack of violating international law by failing to distinguish between military and civilian targets, as well as using prohibited landmines in everyday equipment that could endanger civilians. Meanwhile, security analysts warn this could be a sign of a new era of the "weaponization" of everyday objects.
Today, attacks in which "Internet of Things" devices are sabotaged or disabled by intentionally damaging the device's software are becoming increasingly common. Because manufacturers control the software that collects and processes data, these companies have the ability to integrate features that can be upgraded or downgraded. This also allows for "adjustment in how prevention is handled" when companies intentionally reduce this functionality through a strategy of restricting software updates.
A recent example in the marketplace is a dispute between a train manufacturer and a railway company in Poland that rendered several recently repaired trains unusable for months in 2022 because the manufacturer had used remote digital locks.
These examples illustrate the importance of software control in an era of increasingly networked products and infrastructure. Instead of resorting to sabotage or clandestine manufacturing of explosive devices through shell companies, actors can target through software. They can infiltrate manufacturers to manipulate software production, exploit vulnerabilities, or simply attack system networks.
For a long time, security intelligence agencies have emphasized the need to protect critical infrastructure that increasingly relies on digital networks, ranging from smart grids and emergency communications systems to traffic control systems.
In 2021, the Canadian Security Intelligence Agency (CSIS) warned that the exploitation of critical infrastructure by hostile actors would have "serious financial, social, health, and safety impacts" in the country.
Ensuring the safety of the people.
To understand the potential impact, it's necessary to consider even the most ordinary events. A two-day power outage for Rogers Communications customers in July 2022 disrupted internet and mobile services for over 12 million customers across Canada due to a system upgrade error.
The attacks in Lebanon raise the possibility of violations of international law by targeting civilians and using booby traps and landmines. The weaponization of communications equipment in the attacks is under thorough investigation. Former CIA Director Leon Panetta described these attacks as a form of terrorism.
When multiple manufacturers and distributors are involved in assembling a product, the end consumer must be able to trust the integrity of the supply chain that produced and delivered that product. In the case of the attacks in Lebanon, the economic and political impacts are being felt widely, and rebuilding trust will be very difficult.
Beyond considering the consequences of attacks on global supply chains, there are also policy implications for manufacturers of "Internet of Things" goods, requiring enhanced corporate governance practices.
Not long ago, the U.S. Federal Communications Commission (FCC) approved a voluntary “Internet of Things” labeling program for 2024, allowing manufacturers to display the country’s “Virtual Network Trust Mark.” The goal is to help consumers make informed purchasing decisions and encourage manufacturers to meet increasingly stringent cybersecurity standards.
The attacks in Lebanon highlight the need for authorities at all levels to establish appropriate procurement and operational requirements for digital infrastructure. This must include clearly defining who is responsible for operating and maintaining the infrastructure to better ensure public safety in the age of cyber threats.
Source: https://baoquocte.vn/vu-no-may-nhan-tin-o-lebanon-nguy-co-vu-khi-hoa-vat-dung-hang-ngay-291125.html


























































































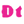




















Comment (0)