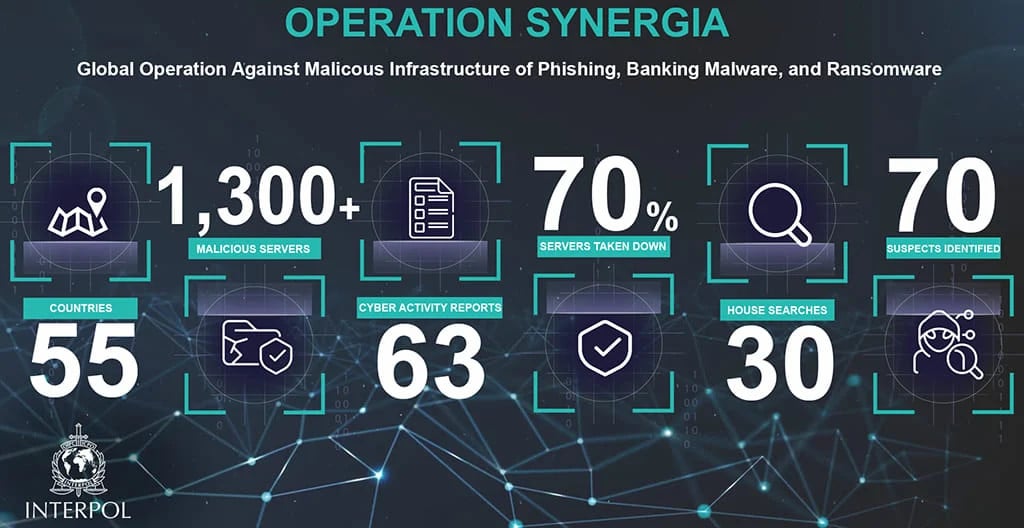
Interpol's operation, codenamed 'Synergia', will run from September to November 2023 and is being launched to respond to the rapid, complex and increasingly professional development of transnational cybercrime networks, as well as the need for coordinated action between countries around the world to combat emerging cyber security threats.
As a result, Interpol discovered more than 500 IP addresses hosting phishing websites and more than 1,900 IP addresses used by malware operators. Authorities arrested 31 individuals and identified 70 other suspects. The operation also found that the malware used by the cybercriminals was distributed on the systems of more than 200 of the world's leading web hosting providers.
The campaign resulted in the takedown of more than 1,300 command and control (C2) servers, accounting for approximately 70% of the detected number. C2s are commonly used in most ransomware, phishing, and malware distribution campaigns. They are used by cybercriminals to control malware in attacks and collect information sent from infected devices, making them an integral part of many attacks.
The scope of 'Synergia' extends to Asia- Pacific , Europe, the Middle East and Africa as well as other regions. Australia, Canada, Hong Kong, Singapore, South Sudan and Zimbabwe are the countries frequently chosen by cybercriminals to launch malware attacks.
In addition to authorities from more than 50 different countries, international cybersecurity companies have also actively participated in Interpol's 'Synergia' operation, notably Group-IB, Kaspersky, Trend Micro, Shadowserver and Team Cymru.
Operation 'Synergia' has proven effective in bringing together international law enforcement, national authorities and private sector partners to collaborate, share information and proactively combat cybercrime.
(according to Interpol)
Source




![[Photo] Explore the US Navy's USS Robert Smalls warship](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F1200x675%2Fvietnam%2Fresource%2FIMAGE%2F2025%2F12%2F10%2F1765341533272_11212121-8303-jpg.webp&w=3840&q=75)


![[Photo] The captivating scenery of the fragrant maple forest in Quang Tri](/_next/image?url=https%3A%2F%2Fvphoto.vietnam.vn%2Fthumb%2F1200x675%2Fvietnam%2Fresource%2FIMAGE%2F2025%2F12%2F10%2F1765353233198_lan09046-jpg.webp&w=3840&q=75)
































![[Video] The craft of making Dong Ho folk paintings has been inscribed by UNESCO on the List of Crafts in Need of Urgent Safeguarding.](https://vphoto.vietnam.vn/thumb/402x226/vietnam/resource/IMAGE/2025/12/10/1765350246533_tranh-dong-ho-734-jpg.webp)










































































Comment (0)