According to BGR , these malicious apps originate from a malware called Anatsa (also known as TeaBot), a particularly dangerous banking malware that appears harmless when users first install it but then downloads malicious code or command-and-control (C2) servers disguised as app updates. This allows the malware to avoid detection on Android app stores.

More than 5.5 million Android apps downloaded infected with Anatsa malware
In other words, the apps are not malicious at first. They trick people into believing they are safe before they proceed to download malicious content disguised as a legitimate app update. Once the malware successfully infects the device and begins communicating with the C2 server, it scans the user’s device for any installed banking apps.
If it finds any information, it sends it to the C2 server, which then sends back a fake login page for the detected apps. If a user falls for this trick and enters their login credentials, the information is sent back to the server, which the hacker can then use to log into the victim's banking app and steal their money.
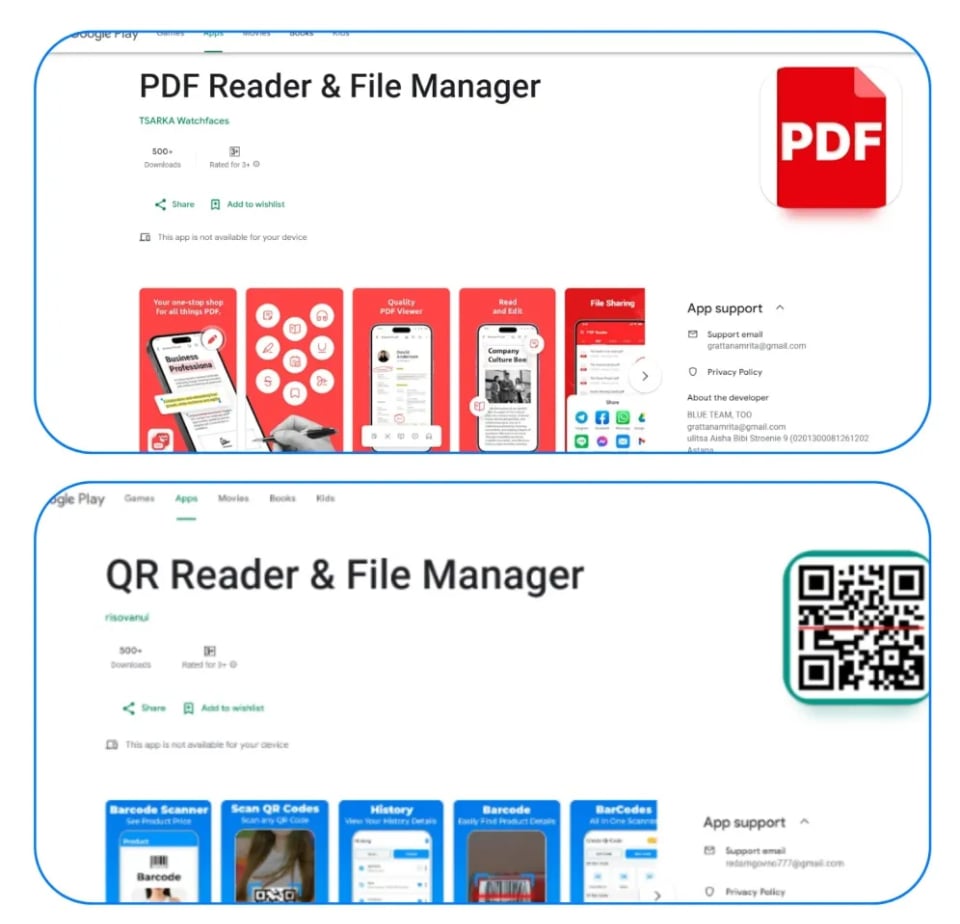
Two of the malicious Android apps named by Zscaler
Two apps that Zscaler found infected with Anatsa include PDF Reader & File Manager and QR Reader & File Manager. Researchers say that Anatsa primarily targets apps from financial institutions in the UK, with victims also found in the US, Germany, Spain, Finland, South Korea, and Singapore. However, experts advise users to be wary of the dangers no matter where they live.
While the researchers did not share the identities of the infected Android apps on the Google Play store, both of the apps shared in the above example are no longer available. Perhaps Zscaler alerted Google to other apps.
Source: https://thanhnien.vn/hon-90-ung-dung-android-doc-hai-tren-google-play-duoc-phat-hien-185240530061227143.htm









































































































Comment (0)